IT Audit
An IT audit is the examination and evaluation of an organization's information technology
infrastructure, policies and operations. Information technology audits determine whether
IT controls protect corporate assets, ensure data integrity and are aligned with the
business's overall goals.
Because operations at modern companies are increasingly computerized, IT audits are used to ensure information-related controls and processes are working properly. The primary objectives of an IT audit include:
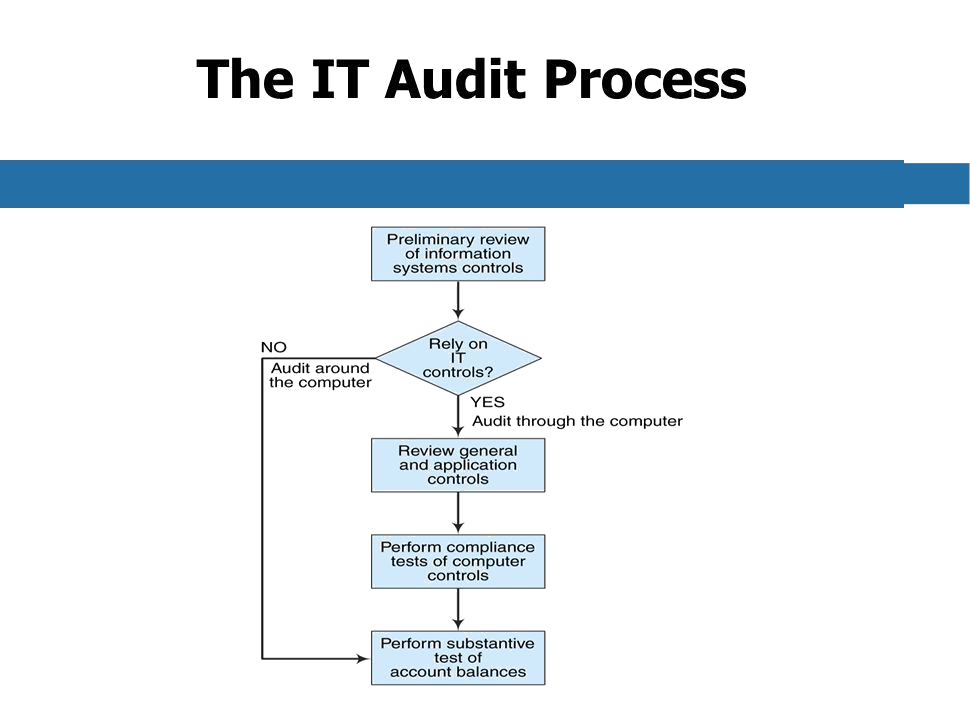
An IT audit can be defined as any audit that encompasses review and evaluation of
automated information processing systems, related non-automated processes and the
interfaces among them. Planning the IT audit involves two major steps. The first
step is to gather information and do some planning the second step is to gain an
understanding of the existing internal control structure. More and more organizations
are moving to a risk-based audit approach which is used to assess risk and helps an IT
auditor make the decision as to whether to perform compliance testing or substantive
testing. In a risk-based approach, IT auditors are relying on internal and operational
controls as well as the knowledge of the company or the business.
This type of risk assessment decision can help relate the cost-benefit analysis of the
control to the known risk. In the “Gathering Information” step the IT auditor needs to
identify five items:
A side note on “Inherent risks”, is to define it as the risk that an error exists
that could be material or significant when combined with other errors encountered
during the audit, assuming there are no related compensating controls. As an example,
complex database updates are more likely to be miswritten than simple ones, and
thumb drives are more likely to be stolen (misappropriated) than blade servers in
a server cabinet. Inherent risks exist independent of the audit and can occur
because of the nature of the business.
In the “Gain an Understanding of the Existing Internal Control Structure” step, the IT
auditor needs to identify five other areas/items:
Once the IT auditor has “Gathered Information” and “Understands the Control” then they are ready to begin the planning, or selection of areas, to be audited. Remember one of the key pieces of information that you will need in the initial steps is a current Business Impact Analysis (BIA), to assist you in selecting the application which support the most critical or sensitive business functions.




